Hacker 101 CTF Walkthrough: Petshop Pro
by Najam Ul Saqib
I am back with another walkthrough to one of the HackerOne's CTF Petshop Pro. Let's look at the interface of this web page.
Flag 1: Now HackerOne gave the hint "There must be a way to administer the app" on this flag, indicating that there must be some sort of admin panel on the website, or maybe some other directories. To know what directories are available on a web server, gobuster tool is the best option.
I used the following command on gobuster.
gobuster dir --url http://34.74.105.127/0244bb7b9a/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt
Let me tell you one thing here, SecLists helped me a lot in this CTF, you should also use SecLists as your go-to wordlist choice. Let's come back to the point. Gobuster gave me some interesting results straightaway.

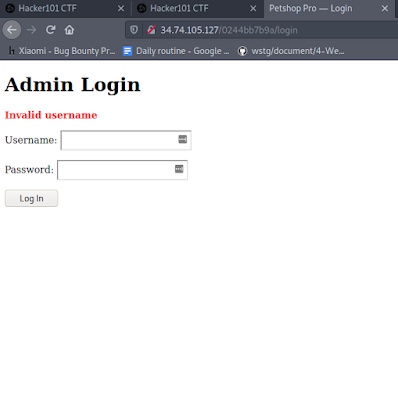
A directory named "/login" has been detected by the tool and this should be the entry point to administer the app. The interesting thing about this login page is that it tells you whether you have entered wrong username or wrong password means that you can be sure of one choice if it's correct or incorrect. This is a bad practice now, one can easily enumerate your username after several tries. For example, if I hit Najam in the username, it straightaway tells me that I have entered an invalid username and that username is something else.
Flag 2: Flag 1 really took me some time, I was hopeless about it
but once you get the flag, the feeling is indescribable. Coming to our 3rd
and final flag. As you can see in the screenshot above that we have got an
"edit" button now on each photo. Why not try simple XSS? The hint was also
pointing towards XSS (Bugs don't always appear in a place where the data is
entered). Let's do it!
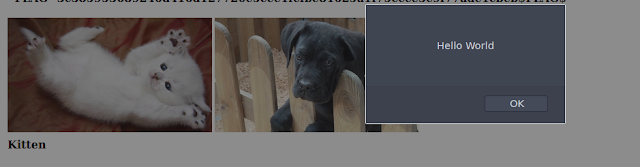
I wrote a smile XSS payload <script> alert('Hello World') </script> into both Name and Description section, as Price section was expecting some numeric data so writing this script there resulted in bad request error. I hit save, went to the homepage, and popup of XSS appeared means the website is vulnerable to Stored XSS.
tags: ctf - hackerone - walkthrough
Flag 0:
This seems like a simple shopping website and remember whenever you see a
shopping website like this, your first area of testing should be checkout.
Whether the web app allows you to shop some free stuff or not? Sounds Cool.
Let's start it this way and try to get some free stuff. Add some stuff into
the cart and move to the checkout page, which will look something like this.
Now I wanted some amount of Kitten photographs. Here you'll be needing the
help of Burp Suite which is a web proxy to intercept (catch) the requests made by the
browser. Set up the Burp proxy, press the "Check Out" button, and intercept
that request.
Under the cart tag, you can see a URL decoded text which is carrying the
products you're trying to check out. As you can see, I have found for 8.95
which is the price of each Kitten's photograph so that I can alter this,
similarly whatever you have added in the cart find its price in the cart tag
and replace it with 0, which means we're turning its price to zero. Like
this.
Now you can see I have replaced all the price information with zero. Now
lets forward this request by hitting the "Forward" button in Burp and here
is your flag 0.
We got the total to 0$. Interesting! Isn't it?
Flag 1: Now HackerOne gave the hint "There must be a way to administer the app" on this flag, indicating that there must be some sort of admin panel on the website, or maybe some other directories. To know what directories are available on a web server, gobuster tool is the best option.
I used the following command on gobuster.
gobuster dir --url http://34.74.105.127/0244bb7b9a/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt
Let me tell you one thing here, SecLists helped me a lot in this CTF, you should also use SecLists as your go-to wordlist choice. Let's come back to the point. Gobuster gave me some interesting results straightaway.

A directory named "/login" has been detected by the tool and this should be the entry point to administer the app. The interesting thing about this login page is that it tells you whether you have entered wrong username or wrong password means that you can be sure of one choice if it's correct or incorrect. This is a bad practice now, one can easily enumerate your username after several tries. For example, if I hit Najam in the username, it straightaway tells me that I have entered an invalid username and that username is something else.
The simple solution to such a scenario is brute forcing, brute-forcing
credentials, as this website is telling us whether the username entered is
right or wrong, so first, we'll try to detect the correct username and
then will look for its password.
Hints available on Hackerone helped me a lot to solve this CTF, I am not
claiming that the way I approached this CTF is the optimal way, but I am
sharing my experience so that one can learn from my experience and
mistakes and I can learn too that where I could have made a better move.
Writing a straightaway, flawless walkthrough post is an easier task but
that makes no sense because there are already such walkthroughs available
in tons.
Anyways, for brute-forcing, you can try multiple tools, Burp, Hydra, etc
but on community version of burp, there is a drawback that on larger
wordlist, the speed of brute-force attack tends to become slower so I
believe Hydra would be a go-to choice in this scenario.
Again I used usernames wordlist (Seclists/Usernames/names/names.txt) from
Seclists, this obviously wasn't my first try, I tried many different
wordlists and default credentials on the login panel and failed, this
flag1 took me a lot of time to discover it. After I found the username, It
was time to check the password against that username.
Once you enter the correct username, the login form now shows the error of
"Invalid Password", its time to hunt for a password. I got a huge wordlist
of 1000000 passwords, it will take you months to brute force such a huge
wordlist through Burp if not years. I wanted an efficient solution, even I
wasn't satisfied with Hydra here as well, Luckily, I came up with
something unique,
Turbo Intruder - A Burp Extension, I just loved this extension (you can view its tutorial by clicking on
its name (hyperlink) I mentioned now), @alibinowax did a wonderful job, he created an amazing extension that was 6000x
faster than usual burp intruder, so obviously that was my way to go... I
started brute-forcing for the password using that gigantic wordlist using
Turbo Intruder and I got the results in o time. I got the password. As I
have got both username and password. I entered and bingo. Got the
flag!
I wrote a smile XSS payload <script> alert('Hello World') </script> into both Name and Description section, as Price section was expecting some numeric data so writing this script there resulted in bad request error. I hit save, went to the homepage, and popup of XSS appeared means the website is vulnerable to Stored XSS.
But looking at the hint again, I went to the "/cart" page, popups do
appear here too, as the product information was being generated from the
database here too, but the name section turned to flag here. Giving out
our last and final flag which we got by exploiting stored XSS
vulnerability in the website.
This was our final flag, Petshop pro was interesting and patience-testing
CTF I would say, I think marking it as an "Easy CTF" would be a bit unfair
because flag1 was not that much easy and piece of cake here. Anyways, Have
an octotastic day!